Prepare for 5th Generation or Gen V Cyber Attacks : Cyber Security Tips
In 2017, WannaCry RansomWare grabed the worldwide attention as thousands of system fell prey to this attack. This cyber attack has been one of the most talked about issues of last year. Even for the year, cybersecurity is one of the top priority sectors of business organizations. The reason is that once an organization gets infected by Ransomware, both its data and reputation comes under jeopardy. As experts are predicting Gen V Cyber Attacks to be prevalent in upcoming days, users should have a comprehensive idea about it. Therefore, we are going to discuss Gen V of cyber attacks & Gen V Cyber security along with the history of cyber crimes.
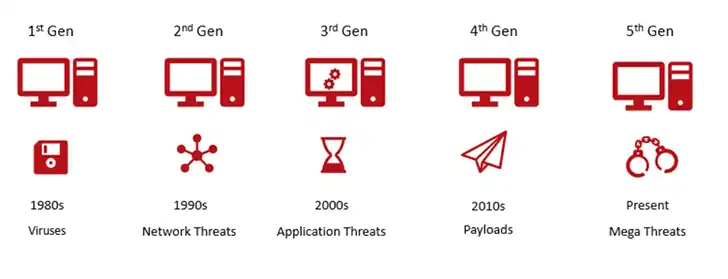
A Brief History of the Generations of Cyber Attacks
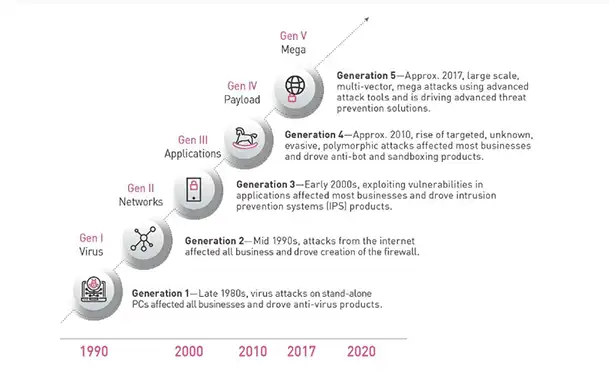
The cyber crime attacks can be categorized into five different generations:
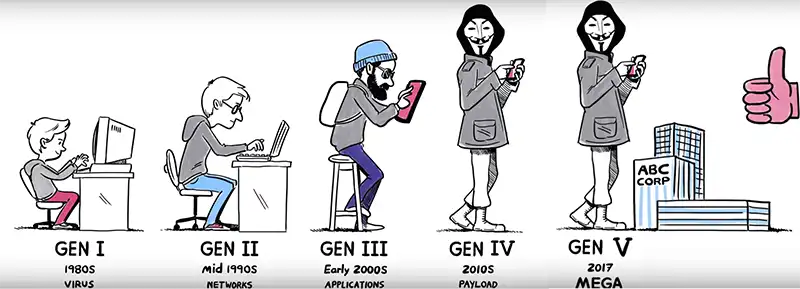
1st Generation:
The very first generation of cyber attacks were virus infection and it used to get contaminated by floppy disks. The time was late 1980s, when floppy disks were used to transfer file between stand-alone PCs. It is the time when the world saw the emergence of anti-virus products.
2nd Generation:
The second generation of cyber attacks started in mid-1990s, which was the time internet started to become popular. As all businesses were eager to get connected to Internet, it was a great opportunity for the attackers. Once you get connected to Internet, anyone can get inside your network and harm you. To stop this from happening, firewall was created. Firewall started to work as a barrier between your network and the Internet, so that no one can enter your network without your permission.
3rd Generation:
From early 2000s, cyber crimes started to become organized and the third generation of cyber crimes began. The targets of attacks have become specific as mail server, web server and applications as criminals realized it can be a source of income for them. They started to steal personal and corporate information. Since Firewall was not enough to prevent this type of attacks, intrusion-prevention products started to develop.
4th Generation:
Red October, a cyber attack launched in 2007 is considered as the beginning of 4th generation of cyber attacks. In this particular phase, the attacks become better engineered as they got backed by more funding. Attacks of this era were done using tools that can easily get inside any vulnerable machine and steal data from it. Technologies like sandbox and anti-bot were introduced during this time.
5th Generation:
When large scale cyber attacks started to emerge in 2017, the 5th generation of cyber attacks or Gen V Cyber Attacks is considered to begin. These mulch-dimensional attacks are often state-sponsored and use the technology developed by state-organizations that somehow leaked to the public. Users should be more aware than ever as this attacks can appear on network, mobile device, and even in cloud. Some infamous 5th generation cyber attacks are WannaCry, SamSam, and Petya.
Where the Risk Lies
After WannaCry attack, enterprises have started to take preventive measures. Unfortunately, most of the organizations still use 2nd and 3rd generation preventive measures that are not capable to fight 5th generation cyber attacks. Many organizations also claim they are completely protected using the 4th generation protective measures. Now, it is obvious that outdated technologies will not be able to detect any recently emerged attack.
In a recent survey, it has been discovered that a shocking 97% of the organizations are not prepared against Gen V Cyber Attacks. With only 21% organizations having any sorts of cyber threat preventive measures tells the story of poor preparation against 5th generation cyber attacks. Enterprises stated that outdated security measures, staffing issues, and conflict with user experience or business system are the main reasons behind this lacking.
Are You Prepared for Gen V Cyber Attacks?
It is possible that the world might see more powerful malware attacks than WannaCry in coming days. If you are a business owner, then you must be completely prepared to protect your organization from these vicious attacks. Users should use multifaceted yet a consolidated Gen V Cyber security measure to protect the entire infrastructure of their organization including mobile devices, cloud

