Transmit The Data With Encryption – The Secure Way For Data Sharing

Data Encryption
Day by day we have modern techniques for distinct purposes. Data encryption is a technique that is not new for computer data security but the method is more enhanced nowadays. The long cipher or key code that cannot be decoded easily is known as encryption method. There are two types of encryption techniques named as Symmetric and Asymmetric encryption those are commonly used by computer users for safe transaction of their confidential files or information. Within this article, you can get knowledge about importance of these algorithms as well as you can know the benefits and pitfalls of these data security patterns.
Know More About Symmetric And Asymmetric Encryption
- Symmetric Key Or Secret Key Encryption: A string of letters, a word, or a numeric number for altering the actual message sent from someone to other safely is known as a secret key that assists for transferring the data over a network or without a network. No chances of data loss or data threatening because, this secret key will be known to sender and receiver only. So when someone wants to unlock the message then, decryption can easily done using this secret key.
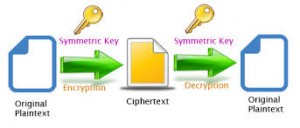
Symmetric Key Encryption
- Asymmetric Key Or Public Key Encryption: Oftentimes secret key encryption creates issues because, if anyone find out the key then, s/he can unlock the file or folder. The issue comes around when data or file is shared over a network where multiple users are available. If anyone knows the pass key that is secret key then, your confidential data may go to the wrong hands. To avoid such kind of problems, the concept of Asymmetric keys came into existence. Here you will have to create two keys- Public and Private, the public key for all the recipients so they can send a message to you and the private is only for you. Any file or document applied with Public key will be decrypted using the same algorithm but, the private key should match. The drawback of symmetric algorithm is resolved by Public key but, in comparison to secret key algorithm public key algorithm is slower. The reason behind it is consuming more power to decrypt and encrypt the data.
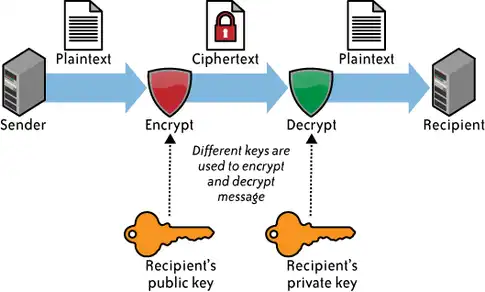
Asymmetric Key Encryption

