Significance Of MD5 Algorithm In Forensics

MD5, the hash value that lets the users to be sure about the email data integrity is became a crucial function for email forensic examiners. This article will assist you to understand:
- What is MD5 Hash?
- What is MD5 Algorithm?
- Where MD5 Checksum values are applicable?
- How MD5 algorithm works?
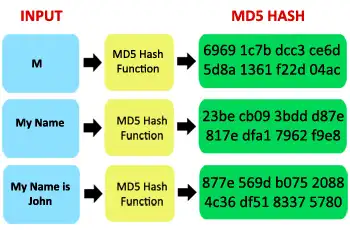
MD5 Hash: Creating a unique 128-bit message digest value from the input no matter how long or small it is plays the role of identifier for an email and it is called as Hash Value. It assists to check out the integrity of emails. With public key encryption, this value assists to create a secured key for compress files as well.
MD5 Algorithm: The logic behind this algorithm is to take text or binary input and creating the hash value that must be of fixed size. The output has value will always be in a fixed manner whether input values may have any length.
Scenario Where MD5 Algorithm Is Helpful
Say you have downloaded a file from internet and you are not sure about its integrity as well as during download the data may prompt to corruption due to given reasons:
- Interrupted internet connection
- Tampering of file due to virus infection
- Attack by any hacker
This scenario compels to extract a MD5 hash value or checksum value for the file so; you can check out that the data is not altered. Hash value will be like:
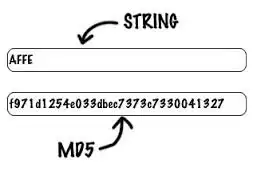
It is not easy to create a Hash value by own so, you can take help of a commercial Hash Value Generator.
How To Apply MD5 Algorithm On Files?
Say you have downloaded mymusic.rar file from an email, and you want to cross check the integrity of this file.
- Create Hash Check-sum using third party hex- value generator or you can try command prompt code available at internet for generating Hash value

- Get hash value of the file before downloading it and as well you will have to get the hash check-sum for the same file after downloading, compare both of these hex hash values


