Discover How to Protect Your PC from Ransomware Attacks
Technology has constantly been turning tables since its existence. As a result, our preferences expanded, priorities changed, and objects replaced. On top of that, our definition of valuable entities too has completely been revised.
Earlier it used to be PEOPLE that we valued the most, while now, it is our DATA. Therefore, more than people, the data is vulnerable of being misused or exploited. Since the origination of big data concept, most number of activities (especially wrongful) revolves largely around the data sector.
Ransomware
Ransomware is one such acts involving significantly crucial amount of data. The right set of people know exactly how vulnerable we all have become, to being affected by such virtual form of extortion, owing to our excessive dependence on DATA.
~Ransomware is the seizure of significantly valuable set of data, with the help of encryption. Data remains encrypted until the victim gives up and gives away the extortion money demanded in exchange of their data.~
The Ransomware Attack and Its Different Forms
Primarily two types of ransomware exist today, that are:
- Locker: User’s computer is locked with the purpose of denying overall access to the entire device and its data.
- Crypto: Locks up files or data preventing access to them with or without encryption, but most cases involve encryption.

The following blog takes you through a collection of information detailing about – Ransomware, its evolution over the past years, consequences, and preventive measures to protect computer from ransomeware attacks.
Ransomware Victims on Target
When all else fails, we approach technology, and so do the culprits. Therefore, though the targets of such attacks could be just anyone but a specific set of user groups are generally the soft targets, some are listed below:
- Home Based Users
- Businesses/Enterprises
- Government Agencies
- Financial Institutions
- Industrial Businesses
- Academic Institutions
- Small Scale Business/Self Employed People
- Law Enforcement Agencies
Pay or Lose – Confirms FBI
Everybody is a potential victim as far as ransomware is concerned. Nevertheless, once caught in the situation, there is no way one can escape from it unless a precautionary measure had been taken previously.
FBI states the following regarding the attack:
- The type and level of encryption used in a ransomware attack is solid
- The only way to get back lost data is to pay for the ransom demanded
- The culprit cannot be tracked owing to the evolution in payment methods
NOTE: Despite the facts pointed out above from the statement of an FBI official, it is not completely impossible to break free and protect PC from Ransomware attack. The adverse consequences of such an attack can be defended with previously taken preventive measures.
Common Entry Points
Nothing in the world is free including the malicious viruses, because you eventually end up paying a price for it. Ransomware can never be forced upon a user and is always a result of the user’s carelessness. The lack of awareness about internet usage policies result in such situations.
Infected websites with:
- Free media download
- Free software
- Malware links
- Malicious popups
Emails with:
- Faulty URLs embedded
- Infected attachments
Evolution in Fund Transfer Medium
During the initial stages, everything is fresh and faulty. Time brings perfection comes into being with experiences attained. There has been a huge evolution in the pattern of transferring funds during a ransomware:
- Transfer via Account ID: Earlier, the ransom was demanded through wired transfer of funds to the suspect’s account considering that the victim(s) had no option, but to pay. However, the approach failed as the culprit was traceable through the account.
- Transfer via Cryptocurrency: The method of fund transfer evolved hugely with the introduction of cryptocurrencies like; Bitcoins. These currencies being virtual and encrypted at the same time make fund transfer untraceable in cases of ransomware.
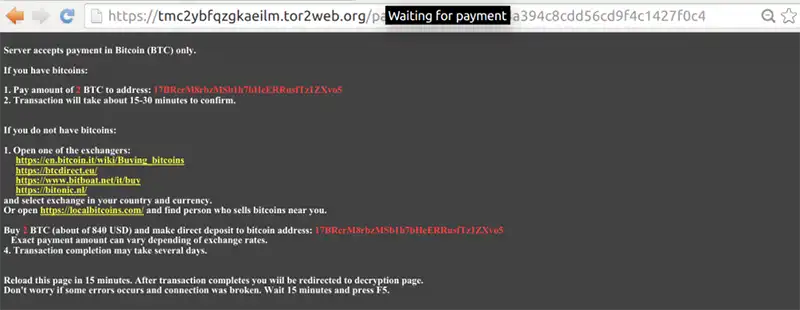
How to Protect Your PC from Ransomware?
Following are the measures define in order to protect computer from ransomeware:
- Backup is the Key: Ensure to keep a full backup of your complete data on an external device as well as on cloud, which should be updated regularly.
- Verify Email Attachments: Phishing is common these days. Thus, verify not only the email but also its attachments before accessing or downloading them.
- Authenticate Hyperlinks: Before clicking on the hyperlinks verify their authenticity by simply placing the cursor upon them and checking the URL associated to it.
- Enable Firewall Settings: Always keep the Windows Firewall settings enabled to shield your system from malware, spyware, and other malicious elements.
- Enhance Browser Settings: See to it that you browser is capable enough to detect and scan compressed and archived files before downloading them.
- Disable Windows Script: Windows Script Host is a potential threat in cases of ransomware therefore disabling them is a great preventive measure.
- Strong Password Usage: Using a combination of multiple characters for generating passwords is strongly suggested to ensure brute-force success.
- Disable Autoplay Setting: With the advancement in technology the mediums of ransomware attacks have also evolved, which includes USB drives therefore, disable autoplay.
- Disable Unused Connections: Ensure that unused connections are disabled like; Bluetooth or WiFi so that no one can interpret them and invade your privacy.
- Implement Software Restriction Policy: Avoid executable files from being run automatically by redefining the software restriction settings on the system.
Concluding:
The usage of high-end algorithms for implementing the encryption has already upped the level of ransomware attacks. In addition to that, the usage of cryptocurrency and Bitcoin in combination with the increase in data connectivity worldwide with poor business continuity measures has made it nearly impossible to curb the attacks and trace the culprit count in such cases. With the right knowledge of internet usage policies and measures to maintain business continuity is the only way that can help a mass user base from different walks of life, defend themselves from such attacks.

